
4 Steps to Block an IP Address for Better Website Protection
Are you worried about unauthorized access to your network? Block an IP Address helps to protect your network from unwanted access and threats. Removing unwanted visitors helps to improve security and performance.
This tutorial will cover how to restrict IP addresses from causing security harm.
Key Takeaways
-
What are the aspects of an IP address, and how it works?
-
Differences between IPv4 and IPv6 and their use.
-
7 reasons to restrict IP addresses for better security.
-
How blocking IP stops unauthorized access.
-
4 steps to block an IP address accessed by CloudPanel.
-
Common methods to restrict IP on your website.
-
Importance of IP Address Blocking: 7 Key Reasons for Network Security & Privacy
-
7 Benefits of IP Address Blocking for Enhanced Security and Performance
What is an IP Address?
An IP address, or Internet Protocol address, is a unique numerical label. It is assigned to every device in a computer network that uses the network rule for communication.
An IP address helps devices communicate within a network. It helps to direct data to the correct location. Your device is given an IP whenever you join the internet. This address can stay the same (static) or change over time (dynamic). The address you want to restrict could be linked to:
-
Unwanted traffic
-
Malicious activities
-
Security threats.
Blocking particular IP addresses helps stop unauthorized access. They help to limit harmful addresses from harming your system. You can block a particular IP using your security configurations or gateway. For example, Windows can help you deny access from problematic addresses. In addition to blocking unwanted IP addresses, using a cheap dedicated IP VPN can help maintain secure and consistent access to your network while reducing exposure to potential threats.
How do IP Addresses Work?
Network Protocol works like a language. It has rules to send and receive data between devices. Devices can talk to each other if they speak the same protocol, no matter where they are. The following is the process of how IP works:
-
Device Connection: Your device connects to a local network with internet access. At home, this network is usually your Internet Service Provider (ISP); at work, it’s the company network. The IP assigned to each linked device helps it communicate.
-
IP Address Assignment: Your ISP gives your device an IP address. This address is used to send and receive data.
-
Routing: Your internet activity goes through the ISP, which uses your IP to send data back to you. The IP can help the ISP find and connect your device.
-
IP Address Changes: If you reset your router or the ISP changes it, your IP can change. You can also block your IP to stop unauthorized access to your network.
-
Traveling with Your Device: If you travel and use a new Wi-Fi network, you will not use your home address. For example, using the network in a hotel or coffee shop. Instead, users will get a temporary IP address from the local network.
Understanding how IP addresses work helps you manage your network better. Users need to block the IP of a device, causing harm or blocking access to a particular IP. They should know how to block them, which can enhance your online security. Restricting IP addresses helps protect your network and improves network management.
2 Types of IP addresses: Old vs New Version
IPv4 and IPv6 are two versions of IP addresses. Both are used to identify devices on the Internet, but they are different in many ways.
1. IPv4 (Internet Protocol version 4)
IPv4 is the older version. It uses a 32-bit address, which means there are about 4.3 billion unique IP addresses. These addresses are written as four numbers separated by periods (e.g., 192.168.1.1). As more devices join the Internet, old IPs are running out.
-
IPv4 is still used the most, but not all devices have enough addresses.
-
It is the primary protocol for devices that connect to the internet.
-
Old IP addresses can be assigned dynamically or statically.
-
Many networks use NAT (Network Address Translation) to handle the shortage of old IPs. This allows multiple devices to share one IP.
-
Old IPs are simple to set up and work with most devices.
2. IPv6 (Internet Protocol version 6)
IPv6 is the newer version designed to solve the problem of limited IP addresses. It uses a 128-bit address format and allows for almost unlimited addresses (about 340 undecillion). Its addresses are written with eight groups of hexadecimal digits (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334).
-
Next-gen IP provides enough addresses for all devices on the internet.
-
It supports auto-configuration, which makes setting up devices easier.
-
Next-gen IP has built-in security features like IPSec, which protects data on the network.
-
With next-gen IP, NAT is unnecessary because every device gets its unique address.
-
It is designed to work alongside old IP but will replace it in the future.
-
More devices are adopting it, and will help the internet grow.
Importance of IP Address Blocking: 7 Key Reasons for Network Security & Privacy
| Reason | Details |
|---|---|
| Blocking Bots and Hackers | Bots, spammers, and hackers can slow down your website, steal data, and hurt sales. Restricting IPs from these sources can stop the damage. |
| Controlling Network Traffic | Restricting IPs from certain areas can help control traffic to your website. It can improve site performance and reduce server strain. |
| Limiting Website Access | Network administrators can restrict a range of IPs to limit what websites employees or students can visit. It helps increase focus and productivity. |
| Enhancing Privacy | If you are being harassed or stalked, restricting IPs can protect data privacy. It helps to stop unwanted IPs from connecting to your network. |
| Protecting Sensitive Data | Hackers often try to steal sensitive data. Restricting IP from accessing your site helps keep that data safe. |
| Complying with Legal Requirements | Businesses may need to deny access from certain countries to follow trade laws or copyright regulations. It helps ensure compliance with legal rules. |
| Maintaining Confidentiality | Organizations with sensitive records, like health or academic data, block specific IP addresses to block unauthorized entry. It keeps important data private. |
How does IP Blocking Work?
IP restriction works by blocking traffic from a particular IP address. It prevents unwanted or harmful traffic from reaching your website or network. The following is the process of how it works:
1. Identifying Malicious IPs
The first step is finding the IP address range you intend to block. You can do this by checking network logs or using tools that detect potential threats. Once you find the harmful IP, you can block it.
2. Configuring the Block
You can restrict an IP using a Windows Firewall or a control panel.
-
Open Windows Firewall and click on “new rule”.
-
Set the rule to block the connection from the identified IP address or IP range.
-
You can block multiple addresses if needed by blocking an IP span.
3. Denying Access
After setting the rule, restricted IP addresses cannot connect to your system. This helps to prevent unauthorized access and helps improve your security.
4. Monitoring and Updating
It is important to monitor your data flow to ensure no other IPs are trying to cause harm. You can remove an IP from the deny list through your security settings or control panel if needed.
5. Restrict a Range of IPs
If you see many IP addresses from the same source, you can restrict an IP range instead of just one. It can stop attacks from multiple addresses coming from the exact location. Restricting IP helps protect your system or website from potential threats. You can block the IP to stop access, even if someone uses a proxy. Additionally, in the face of potential threats, blocking access through the use of fast mobile proxy servers can be a proactive security measure.
6. Using Advanced Settings
You can set specific rules to block certain IPs in the custom settings. For example, you can block new addresses or limit inbound traffic from particular areas. It helps create a safer environment for your network or site.
7. Finalizing the Block
Once the rules are set, apply the rule to ensure the restricted addresses can no longer access your website or network.
4 Steps to Block an IP Address Using CloudPanel
Step 1: Go to the IP Blocking Section
-
Log into your CloudPanel account with your username and password.
-
From the dashboard, go to the IP Blocking section.
Step 2: Click on "Add IP"
At the top right, click on "Add" to begin blocking an IP address.
Step 3: Enter the IP Address
- Type the IP address you want to restrict. You can use either IPv4 or IPv6 format.
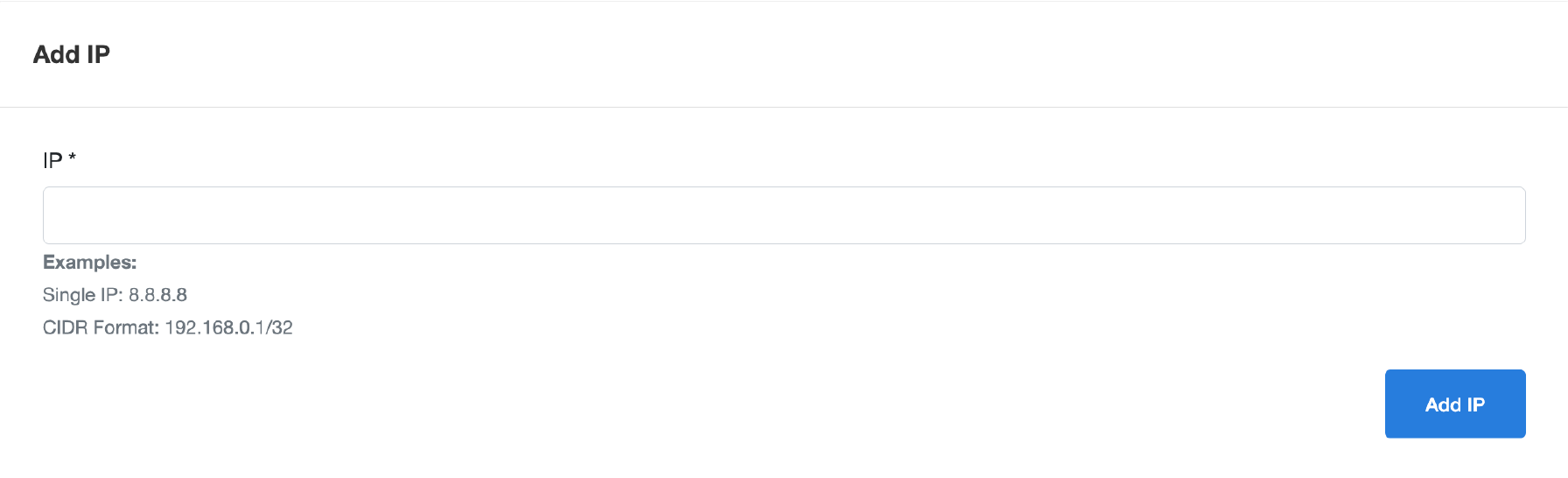
-
For example:
-
IPv4: 8.8.8.8
-
IPv4 CIDR: 192.168.0.1/32
-
IPv6: 2400:6180:100 :d0::99b:5001
-
-
These IP addresses will be blocked from accessing your system.
Step 4: Save the Block
-
After entering the IP address, click Add the IP to save the block.
-
This will stop the IP address from accessing your website or network.
7 Benefits of IP Address Blocking for Enhanced Security and Performance
1. Prevent Unauthorized Access
Blocking unwanted IP addresses stops unauthorized users from accessing sensitive systems and data. For example, Citibank blocks these addresses from regions with high fraud risks. This ensures that only trusted users can access sensitive financial data. Learn how to restrict IP addresses linked to high-risk areas to prevent breaches.
2. Reduce Spam and Unwanted Traffic
Spam and unwanted traffic from bots or spammers can slow down your website. Businesses improve performance and reduce server load by removing spam or fake traffic. For example, Cloudflare blocks millions of suspicious IPs based on addresses daily. This helps keep websites running smoothly.
3. Protect User Privacy
Blocking specific IPs protects users from privacy breaches. For example, Facebook and Instagram restrict IPs from regions known for hacking attempts. This helps keep user accounts and personal data safe. Learn how to restrict IP addresses from risky areas to protect privacy.
4. Manage Bandwidth Usage
Managing bandwidth ensures all users get fair access. Businesses can distribute resources evenly by restricting IPs that use too much bandwidth. For example, Netflix blocks these IP addresses that exceed usage limits. This keeps the network running well for all users.
5. Ensure Regulatory Compliance
Regulations often require restricting addresses from certain regions. For example, Google blocks these IP addresses outside the European Union to comply with GDPR. This helps ensure they follow privacy laws and avoid legal issues.
6. Address Disputes
Restricting IP helps solve issues like harassment or copyright violations. For example, Xbox Live denies IPs from users who cheat or harass others. This keeps the online environment safe for everyone.
7. Enhance User Experience
Blocking harmful traffic helps improve user experience. For example, Amazon Web Services (AWS) blocks harmful IPs to prevent DDoS attacks. This ensures users can access services smoothly and enhances access to your website.
3 Common Methods to Block an IP Address
1. Restrict an IP Address on a Router
-
Make sure you have the correct permissions.
-
You can access your gateway’s web interface using its IP address (e.g., 192.168.1.1 or 192.168.0.1) and login credentials.
-
Find settings like firewall rules, security, or access controls.
-
Look for internet filtering and enter the IP addresses you want to block.
-
Save the settings and test to ensure the IP is blocked.
2. Restrict an IP Address via a Firewall
-
Log in to the security console with admin credentials.
-
Find options for IP filtering.
-
Click on “Add” to create a new rule.
-
Set up the rule based on your needs.
-
Choose to deny or block the connection to stop traffic from the IP address.
-
Enter the IP address or range of addresses you want to block.
-
If needed, specify the destination network or device.
-
Choose the protocol (e.g., TCP, UDP, ICMP) to block.
-
If needed, specify the port number for the traffic.
-
Save the rule and test to check that it works.
3. Restrict an IP Address on Windows
-
Open the Control Panel by clicking the Start button.
-
Go to System and Security > Windows Firewall.
-
Click Advanced Settings.
-
Go to the Outbound Rules tab.
-
Click on “New Rule” and choose Custom Rule.
-
Select This program, browse, and pick the associated program or service (or leave it blank).
-
Choose the correct protocol (e.g., TCP, UDP).
-
If needed, specify the relevant ports.
-
Choose Remote IP addresses and type the address to block.
-
Select Block the connection.
-
Choose which profiles (Domain, Private, Public) the rule should apply to.
-
Name the rule and click Finish to create it.
7 Best Practices for Effective IP Address Blocking
| Best Practices | Details |
|---|---|
| Update IP List | Keep your restricted IP list updated to protect against new threats. Regular updates help block unauthorized entry and middle attacks. |
| Automate Tools | Use automated tools to find and block harmful IPs quickly. This reduces mistakes and speeds up the process, keeping things efficient and timely. |
| Monitor Traffic | Check network traffic and logs regularly for unusual activity. This will help you spot security risks and take quick action. Monitoring also gives you the latest information. |
| Collaborate with Experts | Work with other experts to share harmful IPs. This keeps you informed and strengthens your network's protection. Working together builds a stronger defense. |
| Use blacklist & Whitelist | Block harmful IPs with blacklisting and allow trusted sources with whitelisting. This gives you control over who can connect to your network. It reduces unauthorized access. |
| Stay Informed | Keep learning about new IP-blocking methods. This helps improve security and stay ahead of new threats. Being updated will also allow you to adapt to changing risks. |
| Implement Rate Limiting | Limit the number of requests an IP can make in a specific time. This helps to protect data against DDoS attacks and reduces overload. Rate limiting ensures fair use of resources. |
FAQs
1. How to hide your IP address when surfing the web?
Use a VPN or proxy server firewall to hide your IP address. These tools mask your actual IP and keep your browsing private. This helps protect your online activities and keep them anonymous.
2. Can I block a range of IP addresses using my router?
You can restrict a range of IPs by changing your gateway’s settings. This stops multiple devices on the same network from connecting to your system. It’s helpful if you intend to block an entire network.
3. How can I prevent unwanted traffic from specific IP addresses?
Find the IP address you want to restrict and add it to your security block list. It stops traffic from that IP from reaching your network. Regularly updating your deny list helps prevent new threats.
4. How do I deny IPS access to my website?
To restrict IPS, go to your firewall settings, click "add", and enter the IP you want to block. This will stop those IPS from accessing your site. Denying IPS reduces the risk of bot attacks and spam.
5. What is the role of the domain name system in restricting an IP address?
The domain name system (DNS) ensures blocked IP addresses cannot access your website. It stops requests from those IPs from reaching your server. This helps protect your site from unauthorized access.
Summary
Blocking an IP address stops certain devices from connecting to your network or website. You can add these addresses to a deny list through your security barrier or gateway. It helps protect your system from threats from the attacker. Consider the following reasons to ensure a secure network:
-
Block harmful bots, spammers, and hackers to safeguard your network from threats.
-
Protect sensitive data from unauthorized access by blocking harmful IPs.
-
Comply with legal requirements by blocking IPs from regions that violate laws or regulations.
Explore Cloud Panel Free Hosting and block an IP address to secure your website instantly.



